Private keys are just about the most important things in crypto. In fact, private keys are worth as much as the cryptocurrencies they protect. This is because holding a private key gives you full access to its wallet and the freedom to spend all its assets.
If someone found or stole your private keys, your crypto is their crypto. Stolen keys accounted for more than 40% (around $305 million) of crypto losses in 2024. So, you don’t want your private keys falling into the wrong hands.
This is why private keys are typically not stored like any other piece of data. They have to be encrypted first. Anytime you want to access your keys from the encrypted file, you’ll have to recover them, typically using a password.
But what if you don’t have this password? Well, here is everything you need to know about encryption, including what could go wrong and how to conduct private key recovery.
Understanding Encryption
Encryption is the process of converting data into a coded format to prevent unauthorized access. The original information is known as plain text, and after encryption, it becomes ciphertext.
To use the data, you need to convert ciphertext back to plain text in a process called decryption. Decryption can only be accomplished using the appropriate key, which should only be in the hands of authorized personnel.
Encryption is a pretty old technique of data protection. An early example is the Caesar cipher. Used in correspondence, it involved replacing one letter with another letter, a fixed number of positions down the alphabet.
In modern times, encryption is done with algorithms designed along various cryptographic standards.
Types of Encryption
The two most common types of encryption are symmetric and asymmetric.
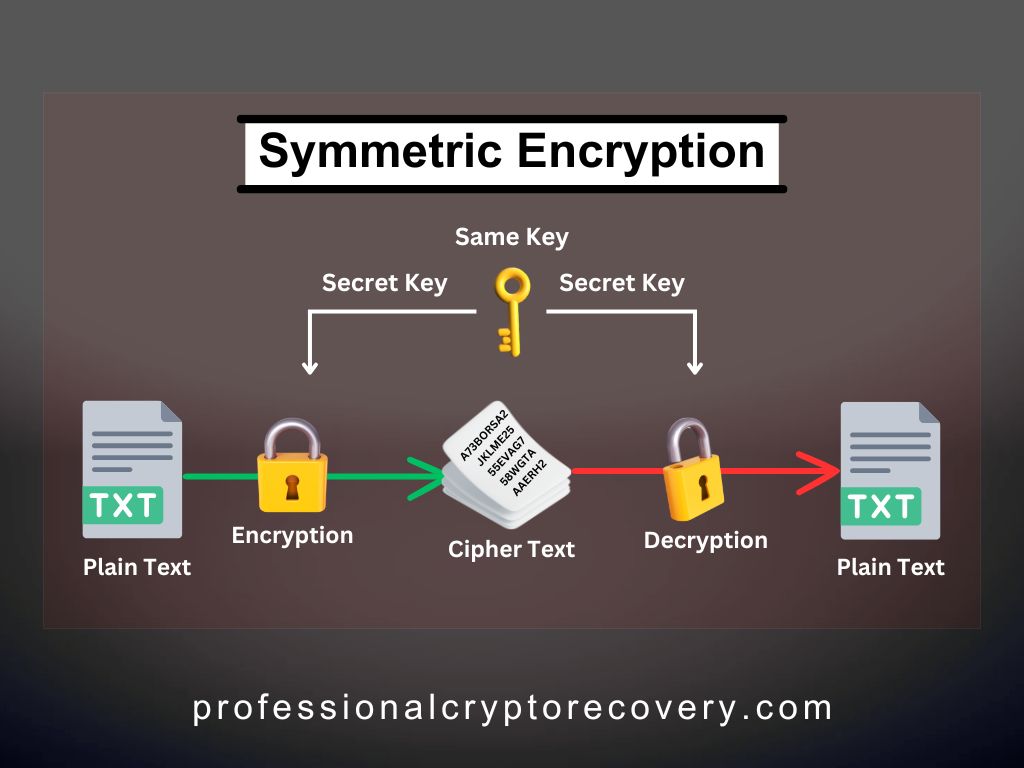
Symmetric Encryption
Symmetric encryption uses the same key for both encryption and decryption. For example, how wallets handle keystore files.
Your wallet encrypts its keystore file using a key derived from your password. This password will be required for decryption any time the file is opened. Most wallets also let you export your private keys as plain text or in a password encrypted file.
If you obtain your private keys in raw format, you’re still advised to encrypt them before storage.
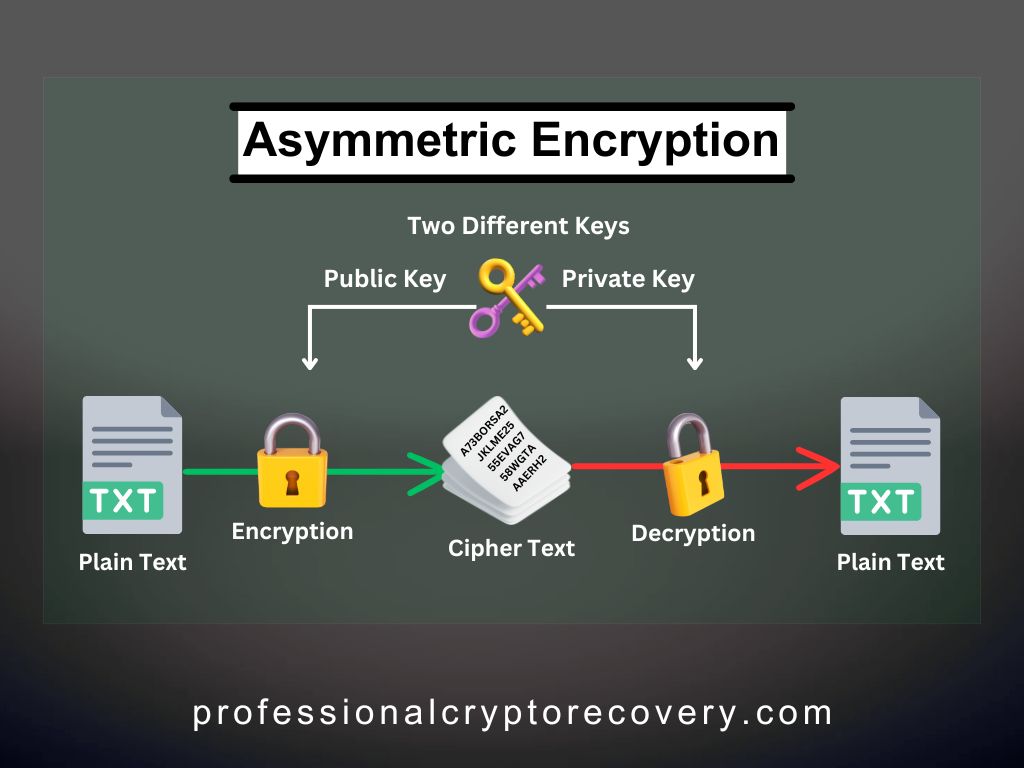
Asymmetric Encryption
Asymmetric encryption uses a pair of keys: one for encryption and the other for decryption.
The encryption key, also known as a public key, is shared among all parties. On the other hand, the decryption key, known as the private key, is shared more selectively. Anyone with the public key can encrypt a message, but only holders of the private key can decrypt it.
This technique lies at the heart of crypto wallets. Your wallet has an address (the public key) that people use to send you assets and a private key, which is used to prove that you own the assets.
So, a crypto wallet’s transaction functionality relies on asymmetric encryption. Then, to protect the private key wherever it is stored, your wallet implements symmetric encryption using your password.
Step-by-Step Guide to Private Key Recovery
Decryption is typically straightforward if you export keystores or other wallet files containing your private keys. You don’t even need to have the same brand of wallet for private key recovery. All you have to do is find a wallet whose software is compatible with the cryptographic standard used by the original wallet and provide the password used to encrypt the backup.
For example, Sparrow Wallet supports importing Electrum keystore files, and MetaMask supports importing MyEtherWallet backup files (and vice versa). When you do this, the wallet application automatically extracts and imports your keys, along with your address and wallet balance.
If You Exported the File Manually
Software wallets also support manual export of their unencrypted private keys, which you’ll have to encrypt for your own safety. This is done using tools like OpenSSL, GNU Privacy Guard (GPG), VeraCrypt, and 7-zip.
Later on, when the need arises, you’ll use the same tool (or another that supports the cryptographic standard) and password to decrypt the file and access your private keys. You can then import these into your crypto wallet as you see fit.
Tips for Decrypting a File Containing Private Keys
- Begin by ensuring you have the correct password and wallet/decryption tool. Some software wallets use different formats and standards making it impossible to directly import/export keystore files between them. For example, Bitcoin Core and Trust Wallet.
The same rule applies to manual decrypting. If the tool you’re using has a different standard from what was used during encryption, it won’t work.
- Work offline, especially if you’re manually decrypting your keys before importing them into your wallet, to minimize exposure to malware or phishing.
One way to go about this is to create an air-gapped virtual machine in your computer and conduct the process there. Then, delete the VM once you’ve obtained your private keys.
- Back up the file before attempting decryption. This ensures you have something to fall back on in case an error occurs and the file is damaged.
Common Challenges and Solutions
Decryption doesn’t always go smoothly. Here are some issues that may come up:
Incorrect Password
Decrypting a crypto wallet file will require the password set during encryption. If the password is incorrect, decryption will fail, making the wallet or its keys inaccessible.
Since crypto wallets are designed for high security, many systems do not allow password recovery. You’ll need to recover the password on your own.
If you remember part of the password, you can attempt recovery using password recovery tools like John the Ripper and Hashcat. This doesn’t always work, in which case, you’ll need the services of a recovery expert.
Corrupted Encrypted File
If the encrypted file containing wallet information or private keys is corrupted, decryption may fail. Corruption can occur due to:
- Incomplete downloads or transfers
- Damage to the storage device
- Malware tampering with the file
Regularly backing up wallet files and verifying their integrity through checksums or secure storage solutions can help mitigate these risks. This ensures that in case of corruption, you have a clean backup.
But if you only have one copy and it’s corrupted, you’ll need to somehow recover your private keys from it. This is a delicate process and will typically require the help of a data recovery expert.
Unsupported or Incompatible Encryption Algorithms
Wallet files encrypted with outdated or uncommon encryption algorithms may not be compatible with modern decryption tools. Issues typically arise if the encryption algorithm requires tools or libraries no longer supported by current systems.
In this case, you’ll need the original software used to encrypt your private keys.
Missing Dependencies or Recovery Data
Decrypting crypto wallet files often relies on more than just a password. Some wallets require additional recovery data. Take files encrypted using initialization vectors (IVs) or salt values, for instance.
IVs and salt are critical in cryptographic systems to enhance security:
- IVs (Initialization Vectors) ensure that even if the same data is encrypted multiple times, the resulting ciphertext will differ.
- Salt values are used in conjunction with passwords to produce unique encryption keys, protecting against precomputed attacks like rainbow tables.
These values are usually stored alongside the encrypted data, but they are essential for decryption. Without them, even the correct password won’t allow access.
Malware or Security Interference
Security software or malware can interfere with the decryption of wallet files. For example:
- Antivirus programs may flag wallet files or decryption tools as suspicious, blocking access.
- Malware could tamper with encrypted files, alter passwords, or steal private keys during the decryption process.
Using trusted wallet software, running regular malware scans, and avoiding unverified tools can help mitigate these risks.
Incomplete Decryption Software Configuration
If the decryption tool is misconfigured, it may lead to errors or failures. Common configuration issues include:
- Selecting the wrong encryption algorithm or mode (e.g., AES-CBC vs. AES-GCM)
- Using an incorrect salt or IV if required by the encryption scheme
This is a relatively simple issue to solve. All you have to do is take your time understanding the wallet’s encryption details and correctly configuring decryption tools.
Need Help With Private Key Recovery?
Encrypting private keys is the standard way to store them. But sometimes, an issue arises that stops you from decrypting your keys and accessing them. If you can’t get past it, don’t count your assets lost just yet; professional crypto recovery got you.
Professional Crypto Recovery specializes in recovering private keys, including from encrypted files. Our services are fast, efficient, and among the most affordable in the market. Contact us today to get started.
FAQs
Can a private key be recovered?
No, a private key cannot be recovered if lost unless you have a backup or recovery phrase. Always store your private key securely, as losing it means losing access to your crypto assets.
How do I access an encrypted private key?
To access an encrypted private key, use the correct password with the associated decryption tool or wallet software. Ensure you have the necessary metadata (e.g., salt or IV) and dependencies required for decryption.
1Password vs KeePass: Where do I store my encrypted private key?
1Password and KeePass are popular choices for securely storing sensitive information. 1Password offers cloud-based convenience with strong encryption while KeePass provides an open-source, offline solution for users who prefer full control over their data.
The latter is more suitable for private keys.
What happens if I forget the password for my encrypted private key?
If you forget the password, you cannot decrypt or access your private key. Without backups or recovery options, your encrypted data and crypto assets may be permanently inaccessible.
Can I use any tool to decrypt my private key?
No, you must use the tool or wallet software compatible with the encryption method used for securing the private key. Using incompatible tools may result in errors.
